Introduction To Computer Security Matt Bishop Exercise Solutions | PDF | Information Security | Computer Security
![Introduction to Computer Security Lecture 2 of Professors Chris Clifton Matt Bishop INFSCI 2935: Introduction of Computer Security 1 September 4, 2003 Introduction to Computer Security - [PDF Document] Introduction to Computer Security Lecture 2 of Professors Chris Clifton Matt Bishop INFSCI 2935: Introduction of Computer Security 1 September 4, 2003 Introduction to Computer Security - [PDF Document]](https://demo.vdocument.in/img/378x509/reader019/reader/2020040110/5abdf16c7f8b9ab02d8c46b5/r-2.jpg)
Introduction to Computer Security Lecture 2 of Professors Chris Clifton Matt Bishop INFSCI 2935: Introduction of Computer Security 1 September 4, 2003 Introduction to Computer Security - [PDF Document]

Computer Security: Art and Science (2 Volume Set): 9780134289519: Computer Science Books @ Amazon.com

Software Security and Security Engineering (Part 1) Software Engineering Sources: Introduction to Computer Security, Matt Bishop, Addison Wesley, ppt download

November 1, 2004Introduction to Computer Security ©2004 Matt Bishop Slide #1-1 Chapter 1: Introduction Components of computer security Threats Policies. - ppt download

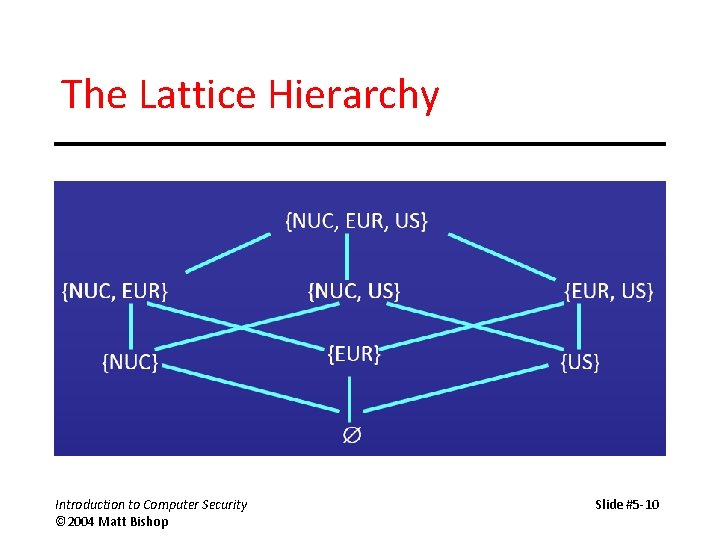
Hybrid Policies Overview Chinese Wall Model Clinical Information Systems Security Policy ORCON RBAC Introduction to Computer Security ©2004 Matt Bishop. - ppt download

Buy Introduction to Computer Security Book Online at Low Prices in India | Introduction to Computer Security Reviews & Ratings - Amazon.in

Computer Security: Art and Science (2 Volume Set): 9780134289519: Computer Science Books @ Amazon.com

Buy Introduction to Computer Security Book Online at Low Prices in India | Introduction to Computer Security Reviews & Ratings - Amazon.in